mardi 17 avril 2012
jeudi 12 avril 2012
nmap
scan réseau rapide
nmap -sP 192.168.1.0/24
scan avec listing des ports ouverts
nmap -p1-1024 192.168.1.0/24
nmap -sP 192.168.1.0/24
scan avec listing des ports ouverts
nmap -p1-1024 192.168.1.0/24
mardi 10 avril 2012
ntop
manager@ubuntu-416:~$ ntop start
Tue Apr 10 15:59:28 2012 NOTE: Interface merge enabled by default
Tue Apr 10 15:59:28 2012 Initializing gdbm databases
Tue Apr 10 15:59:28 2012 **ERROR** ....open of /var/lib/ntop/prefsCache.db failed: File open error
Tue Apr 10 15:59:28 2012 Possible solution: please use '-P <directory>'
Tue Apr 10 15:59:28 2012 **FATAL_ERROR** GDBM open failed, ntop shutting down...
Tue Apr 10 15:59:28 2012 CLEANUP[t3077826240]: ntop caught signal 2
Tue Apr 10 15:59:28 2012 THREADMGMT[t3077826240]: ntop RUNSTATE: SHUTDOWN(7)
Tue Apr 10 15:59:28 2012 CLEANUP[t3077826240] catching thread is unknown
Tue Apr 10 15:59:28 2012 CLEANUP: Running threads
Tue Apr 10 15:59:28 2012 CLEANUP: Locking purge mutex (may block for a little while)
Tue Apr 10 15:59:28 2012 CLEANUP: Locked purge mutex, continuing shutdown
Tue Apr 10 15:59:28 2012 CLEANUP: Continues
Tue Apr 10 15:59:28 2012 PLUGIN_TERM: Unloading plugins (if any)
Tue Apr 10 15:59:28 2012 CLEANUP: Clean up complete
Tue Apr 10 15:59:28 2012 THREADMGMT[t3077826240]: ntop RUNSTATE: TERM(8)
Tue Apr 10 15:59:28 2012 ===================================
Tue Apr 10 15:59:28 2012 ntop is shutdown...
Tue Apr 10 15:59:28 2012 ===================================
Il faut le lancer avec les droits root
sudo ntop
Puis enfin accéder via un navigateur
http://@IP:3000
samedi 7 avril 2012
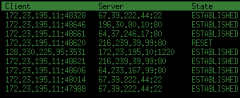
tcptrack
SYNOPSIS
tcptrack [ -dfhvp ] [ -r seconds ] -i interface [ filter expression ]
DESCRIPTION
tcptrack displays the status of TCP connections that it sees on a given network interface. tcptrack monitors their state and displays information such as state, source/des- tination addresses and bandwidth usage in a sorted, updated list very much like the top(1) command. The filter expression is a standard pcap filter expression (identical to the expressions used by tcpdump(8)) which can be used to filter down the characteristics of TCP con- nections that tcptrack will see. See tcpdump(8) for more information about the syntax of this expression.
OPTIONS
-d Only track connections that were started after tcp- track was started. Do not try to detect existing connections. -f Enable fast average recalculation. TCPTrack will calculate the average speeds of connections by using a running average. TCPTrack will use more memory and CPU time, but averages will seem closer to real time and will be updated more than once per second and may be more accurate under heavy load. The number of times per second that averages will be recalculated in fast mode is a compile-time set- ting that defaults to 10 times per second. -h Display command line help -i [interface] Sniff packets from the specified network interface. -p Do not put the interface being sniffed into promis- cuous mode. -r [seconds] Wait this many seconds before removing a closed connection from the display. Defaults to 2 sec- onds. See also the pause interactive command (below). -v Display tcptrack version
INTERACTIVE COMMANDS
The following keys may be pressed while tcptrack is run- ning to change runtime options: When paused (via the p command) no new connections will be displayed, however tcptrack will still monitor and track all connections it sees as usual. This option affects the display only, not internals. When you unpause, the display will be updated with all current information that tcptrack has been gathering all along.
EXAMPLES
tcptrack requires only one parameter to run: the -i flag followed by an interface name that you want tcptrack to monitor. This is the most basic way to run tcptrack: # tcptrack -i eth0 tcptrack can also take a pcap filter expression as an argument. The format of this filter expression is the same as that of tcpdump(8) and other libpcap-based sniffers. The following example will only show connections from host 10.45.165.2: # tcptrack -i eth0 src or dst 10.45.165.2 The next example will only show web traffic (ie, traffic on port 80): # tcptrack -i eth0 port 80 sources
monitor, network
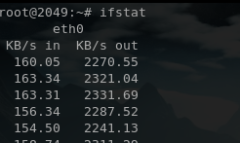
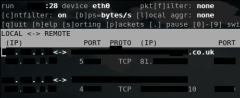
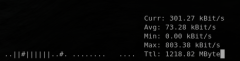
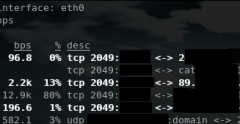
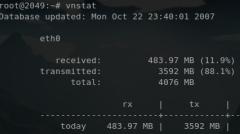
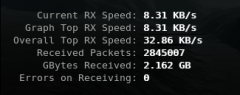
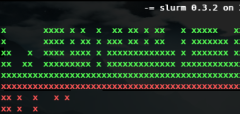
Liste de logiciels permettant de monitorer les interfaces réseau
iperf
ipfm
cbm
ibmonitor
pktstat
mactrack
MRTG
Cacti
sources
http://www.ubuntugeek.com/bandwidth-monitoring-tools-for-ubuntu-users.html
http://e1ement2048.wordpress.com/2007/10/26/herramientas-de-monitoreo/
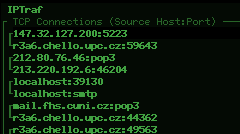
IPTraf
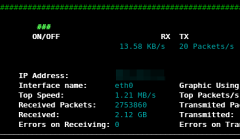
EthStatus
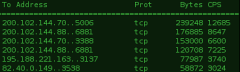
Trafshow
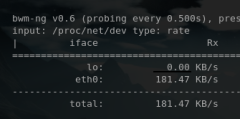
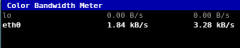
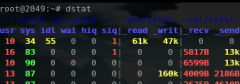
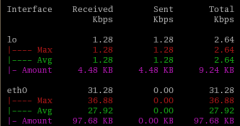
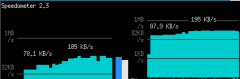
iperf
ipfm
cbm
ibmonitor
pktstat
mactrack
MRTG
Cacti
sources
http://www.ubuntugeek.com/bandwidth-monitoring-tools-for-ubuntu-users.html
http://e1ement2048.wordpress.com/2007/10/26/herramientas-de-monitoreo/
vendredi 6 avril 2012
jeudi 5 avril 2012
syslog reader
sources
http://czanik.blogs.balabit.com/2011/06/a-comparison-of-syslog-ng-web-guis/
http://www.gizeek.com/2010/04/11/centralisation-et-gestion-des-logs-avec-rsyslog-et-loganalyzer/
http://www.opendoc.net/solutions/comment-installer-configurer-serveur-log-syslog-ng
http://blog.pastoutafait.org/billets/CCZE-mettez-de-la-couleur-dans-vos-logs
mercredi 4 avril 2012
antenne, wIfi
http://www.google.com/url?sa=t&rct=j&q=&esrc=s&source=web&cd=2&ved=0CDAQFjAB&url=http%3A%2F%2Fwww.cisco.com%2Fen%2FUS%2Fprod%2Fcollateral%2Fwireless%2Fps7183%2Fps469%2Fat_a_glance_c45-513837.pdf&ei=acZ6T77YE-nE0QXHz9C3CQ&usg=AFQjCNFKScM9UgusLzo7FJ28LDUhoLu2Qw
http://www.tandco.fr/boutique/fiche_produit.cfm?ref=AWUS036NH&type=86&code_lg=lg_fr&num=82
http://www.tandco.fr/boutique/fiche_produit.cfm?ref=AWUS036NH&type=86&code_lg=lg_fr&num=82
ipython, IDE web, scipy
sudo apt-get install ipython
Lancement de l'interface
ipython notebook --pylab
Installer le logiciel pour le calcul mathématique et scientifique sous python
sudo apt-get install python-scipy
Installation du module pylab
sudo apt-get install python-matplotlib
code source
from scipy import *
from scipy.special import jn, jn_zeros
def drumhead_height(n, k, distance, angle, t):
nth_zero = jn_zeros(n, k)
return cos(t)*cos(n*angle)*jn(n, distance*nth_zero)
theta = r_[0:2*pi:50j]
radius = r_[0:1:50j]
x = array([r*cos(theta) for r in radius])
y = array([r*sin(theta) for r in radius])
z = array([drumhead_height(1, 1, r, theta, 0.5) for r in radius]) import pylab
from mpl_toolkits.mplot3d import Axes3D
from matplotlib import cm
fig = pylab.figure()
ax = Axes3D(fig)
ax.plot_surface(x, y, z, rstride=1, cstride=1, cmap=cm.jet)
ax.set_xlabel('X')
ax.set_ylabel('Y')
ax.set_zlabel('Z')
pylab.show()
Sources
http://ipython.org/ipython-doc/stable/interactive/htmlnotebook.html
http://docs.scipy.org/doc/scipy/reference/tutorial/special.html
http://docs.scipy.org/doc/
Lancement de l'interface
ipython notebook --pylab
Installer le logiciel pour le calcul mathématique et scientifique sous python
sudo apt-get install python-scipy
Installation du module pylab
sudo apt-get install python-matplotlib
code source
from scipy import *
from scipy.special import jn, jn_zeros
def drumhead_height(n, k, distance, angle, t):
nth_zero = jn_zeros(n, k)
return cos(t)*cos(n*angle)*jn(n, distance*nth_zero)
theta = r_[0:2*pi:50j]
radius = r_[0:1:50j]
x = array([r*cos(theta) for r in radius])
y = array([r*sin(theta) for r in radius])
z = array([drumhead_height(1, 1, r, theta, 0.5) for r in radius]) import pylab
from mpl_toolkits.mplot3d import Axes3D
from matplotlib import cm
fig = pylab.figure()
ax = Axes3D(fig)
ax.plot_surface(x, y, z, rstride=1, cstride=1, cmap=cm.jet)
ax.set_xlabel('X')
ax.set_ylabel('Y')
ax.set_zlabel('Z')
pylab.show()
Sources
http://ipython.org/ipython-doc/stable/interactive/htmlnotebook.html
http://docs.scipy.org/doc/scipy/reference/tutorial/special.html
http://docs.scipy.org/doc/
pyhon, module
cd /var/www/html
[root@test11 html]# ls
info.php
[root@test11 html]# touch index.html
[root@test11 html]# view index.html
(make your Welcome text message)
[root@test11 html]# python -m SimpleHTTPServer
Serving HTTP on 0.0.0.0 port 8000 ...
localhost - - [04/Apr/2012 11:05:26] "GET / HTTP/1.1" 200 -
localhost - - [04/Apr/2012 11:05:26] code 404, message File not found
localhost - - [04/Apr/2012 11:05:26] "GET /favicon.ico HTTP/1.1" 404
L'option m permet de définir les modules utilisés
-m module-name
Searches sys.path for the named module and runs the correspond‐
ing .py file as a script.
Liste des modules
In
ipythonyou can type "importTab".In the standard Python interpreter, you can type "
help('modules')".At the command-line, you can use
pydocmodules.In a script, call
pkgutil.iter_modules().
lancer ipython
In [2]: import
Display all 573 possibilities? (y or n)
ANSI formatter
AptUrl fpectl
ArgImagePlugin fpformat
BaseHTTPServer fractions
Bastion ftplib
BdfFontFile functools
BmpImagePlugin future_builtins
BufrStubImagePlugin gc
CDROM gconf
CGIHTTPServer gdbm
Canvas genericpath
CommandNotFound getopt
ConfigParser getpass
ContainerIO gettext
Cookie gi
Crypto gio
CurImagePlugin glib
DLFCN glob
DcxImagePlugin gnome_sudoku
Dialog gnomekeyring
DistUpgrade gobject
DocXMLRPCServer google
EpsImagePlugin grp
ExifTags gst
FSM gstoption
FileDialog gtk
FitsStubImagePlugin gtkunixprint
FixTk gwibber
FliImagePlugin gzip
FontFile hashlib
FpxImagePlugin heapq
GbrImagePlugin hmac
GdImageFile hotshot
GifImagePlugin hpmudext
GimpGradientFile htmlentitydefs
GimpPaletteFile htmllib
GnuPGInterface httplib
GribStubImagePlugin httplib2
HTMLParser ibus
Hdf5StubImagePlugin ihooks
IN imageop
IPython imaplib
IcnsImagePlugin imghdr
IcoImagePlugin imp
ImImagePlugin importlib
Image imputil
ImageChops inspect
ImageCms io
ImageColor itertools
ImageDraw jockey
ImageDraw2 json
ImageEnhance keyring
ImageFile keyword
ImageFileIO language_support_pkgs
ImageFilter launchpadlib
ImageFont lazr
ImageGL lib2to3
ImageGrab libproxy
ImageMath libxml2
ImageMode libxml2mod
ImageOps linecache
ImagePalette linuxaudiodev
ImagePath locale
ImageQt logging
ImageSequence louis
ImageShow lsb_release
ImageStat macpath
ImageTransform macurl2path
ImageWin mailbox
ImtImagePlugin mailcap
IptcImagePlugin mako
JpegImagePlugin markupbase
LanguageSelector markupsafe
McIdasImagePlugin marshal
MicImagePlugin math
MimeWriter md5
MpegImagePlugin mhlib
MspImagePlugin mimetools
NvidiaDetector mimetypes
OleFileIO mimify
Onboard miniterm
OpenSSL mmap
PAMmodule modulefinder
PIL multifile
PSDraw multiprocessing
PaletteFile mutex
PalmImagePlugin mx
PcdImagePlugin netrc
PcfFontFile new
PcxImagePlugin nis
PdfImagePlugin nntplib
PixarImagePlugin ntpath
PngImagePlugin nturl2path
PpmImagePlugin numbers
PsdImagePlugin oauth
PyQt4 oneconf
Queue opcode
Quirks operator
ScrolledText optparse
SgiImagePlugin orca
SimpleDialog os
SimpleHTTPServer os2emxpath
SimpleXMLRPCServer ossaudiodev
SocketServer packagekit
SpiderImagePlugin pango
StringIO pangocairo
SunImagePlugin papyon
TYPES parallelmagic
TarIO parser
TgaImagePlugin pcardext
TiffImagePlugin pdb
TiffTags pexpect
Tix pickle
Tkconstants pickletools
Tkdnd pilconvert
Tkinter pildriver
UbuntuSystemService pilfile
UpdateManager pilfont
UserDict pilprint
UserList pipes
UserString piston_mini_client
WalImageFile pkg_resources
WmfImagePlugin pkgutil
XKit platform
XVThumbImagePlugin plistlib
XbmImagePlugin popen2
XpmImagePlugin poplib
_LWPCookieJar posix
_MozillaCookieJar posixfile
__builtin__ posixpath
__future__ pprint
__main__ problem_report
__phello__ profile
_abcoll pstats
_ast pty
_bisect pwd
_bsddb pxssh
_codecs pyHnj
_codecs_cn py_compile
_codecs_hk pyatspi
_codecs_iso2022 pychecker
_codecs_jp pychecker2
_codecs_kr pyclbr
_codecs_tw pycurl
_collections pydoc
_csv pydoc_data
_ctypes pyexpat
_ctypes_test pygst
_curses pygtk
_curses_panel pyinotify
_dbus_bindings pynotify
_dbus_glib_bindings quopri
_elementtree random
_functools re
_hashlib readline
_heapq reportlab
_hotshot repr
_imaging resource
_imagingcms rexec
_imagingft rfc822
_imagingmath rlcompleter
_io robotparser
_json runpy
_locale scanext
_lsprof sched
_multibytecodec screen
_multiprocessing select
_pyio serial
_random sessioninstaller
_renderPM sets
_rl_accel sgmllib
_socket sgmlop
_sqlite3 sha
_sre shelve
_ssl shlex
_strptime shutil
_struct signal
_symtable simplegeneric
_testcapi simplejson
_threading_local sip
_warnings sipconfig
_weakref sipconfig_nd
_weakrefset site
abc sitecustomize
aifc smbc
antigravity smtpd
anydbm smtplib
appindicator sndhdr
apport socket
apport_python_hook softwarecenter_aptd_plugins
apt softwareproperties
apt_inst speechd
apt_pkg speechd_config
aptdaemon spwd
aptsources sqlite3
argparse sre
array sre_compile
ast sre_constants
asynchat sre_parse
asyncore ssl
atexit stat
atk statvfs
audiodev storemagic
audioop string
autoreload stringold
axi stringprep
base64 strop
bdb struct
binascii subprocess
binhex sunau
bisect sunaudio
brlapi symbol
bsddb sympyprinting
butterfly symtable
bz2 sys
cPickle sysconfig
cProfile syslog
cStringIO tabnanny
cairo tarfile
calendar telepathy
cgi telnetlib
cgitb tempfile
chardet termios
checkbox test
checkbox_qt textwrap
chunk this
cmath thread
cmd threading
code time
codecs timeit
codeop tkColorChooser
collections tkCommonDialog
colorsys tkFileDialog
commands tkFont
compileall tkMessageBox
compiler tkSimpleDialog
computerjanitor toaiff
configglue token
configobj tokenize
contextlib trace
cookielib traceback
copy ttk
copy_reg tty
crypt turtle
csv twisted
ctypes types
cups ubuntu_sso
cupsext ubuntuone
cupshelpers ufw
curl unicodedata
curses unittest
datetime uno
dateutil unohelper
dbhash urllib
dbm urllib2
dbus urlparse
deb822 usbcreator
debconf user
debian uu
debian_bundle uuid
debtagshw validate
decimal virtkey
decorator vtemodule
defer wadllib
difflib warnings
dircache wave
dirspec weakref
dis webbrowser
distutils whichdb
dl wsgiref
doctest wx
drv_libxml2 wxPython
dsextras wxversion
dumbdbm xapian
dummy_thread xdg
dummy_threading xdiagnose
duplicity xdrlib
email xml
encodings xmllib
errno xmlrpclib
exceptions xxsubtype
farsight zeitgeist
fcntl zipfile
fdpexpect zipimport
filecmp zlib
fileinput zope
fnmatch
mardi 3 avril 2012
Webmin, firewall
Le script à utiliser pour générer les logs (enfin ca ne marche pas mais je vais voir +tard)
Rules file /var/lib/iptables/active
cat /var/lib/iptables/active
# Generated by webmin *filter :FORWARD ACCEPT [0:0] :INPUT ACCEPT [0:0] :OUTPUT ACCEPT [0:0] -A FORWARD -o eth1 -j LOG --log-level 7 --log-prefix BANDWIDTH_OUT: -A FORWARD -i eth1 -j LOG --log-level 7 --log-prefix BANDWIDTH_IN: -A OUTPUT -o eth1 -j LOG --log-level 7 --log-prefix BANDWIDTH_OUT: -A INPUT -i eth1 -j LOG --log-level 7 --log-prefix BANDWIDTH_IN: COMMIT # Completed # Generated by webmin *mangle :FORWARD ACCEPT [0:0] :INPUT ACCEPT [0:0] :OUTPUT ACCEPT [0:0] :PREROUTING ACCEPT [0:0] :POSTROUTING ACCEPT [0:0] COMMIT # Completed # Generated by webmin *nat :PREROUTING ACCEPT [0:0] :OUTPUT ACCEPT [0:0] :POSTROUTING ACCEPT [0:0] -A POSTROUTING -o eth0 -j MASQUERADE -A POSTROUTING -o eth0 -j MASQUERADE COMMIT # Completed
sources
http://doxfer.webmin.com/Webmin/LinuxFirewall
http://www.adella.org/spip/Configurer-IPTABLES-avec-WEBMIN
http://ubuntuforums.org/archive/index.php/t-1442954.html
http://fsse.info/IpTables
http://fsse.info/WebMinFirewall
http://www.linuxhomenetworking.com/wiki/index.php/Quick_HOWTO_:_Ch14_:_Linux_Firewalls_Using_iptables
#--------------------------------------------------------------- # Log and drop all other packets to file /var/log/messages # Without this we could be crawling around in the dark #--------------------------------------------------------------- iptables -A OUTPUT -j LOG iptables -A INPUT -j LOG iptables -A FORWARD -j LOG iptables -A OUTPUT -j DROP iptables -A INPUT -j DROP iptables -A FORWARD -j DROPLorsque l'on génère les régles pour monitorer le réseau le script est générer à cet endroit mais il n'est pas executé.
Rules file /var/lib/iptables/active
cat /var/lib/iptables/active
# Generated by webmin *filter :FORWARD ACCEPT [0:0] :INPUT ACCEPT [0:0] :OUTPUT ACCEPT [0:0] -A FORWARD -o eth1 -j LOG --log-level 7 --log-prefix BANDWIDTH_OUT: -A FORWARD -i eth1 -j LOG --log-level 7 --log-prefix BANDWIDTH_IN: -A OUTPUT -o eth1 -j LOG --log-level 7 --log-prefix BANDWIDTH_OUT: -A INPUT -i eth1 -j LOG --log-level 7 --log-prefix BANDWIDTH_IN: COMMIT # Completed # Generated by webmin *mangle :FORWARD ACCEPT [0:0] :INPUT ACCEPT [0:0] :OUTPUT ACCEPT [0:0] :PREROUTING ACCEPT [0:0] :POSTROUTING ACCEPT [0:0] COMMIT # Completed # Generated by webmin *nat :PREROUTING ACCEPT [0:0] :OUTPUT ACCEPT [0:0] :POSTROUTING ACCEPT [0:0] -A POSTROUTING -o eth0 -j MASQUERADE -A POSTROUTING -o eth0 -j MASQUERADE COMMIT # Completed
iptables list
iptables list configuration (use iptables -L -n to show numeric ip and port numbers)# iptables -L Chain INPUT (policy ACCEPT) target prot opt source destination LOG all -- anywhere anywhere LOG level debug prefix `BANDWIDTH_IN:' Chain FORWARD (policy ACCEPT) target prot opt source destination LOG all -- anywhere anywhere LOG level debug prefix `BANDWIDTH_OUT:' LOG all -- anywhere anywhere LOG level debug prefix `BANDWIDTH_IN:' Chain OUTPUT (policy ACCEPT) target prot opt source destination LOG all -- anywhere anywhere LOG level debug prefix `BANDWIDTH_OUT:'
iptables logfile
/etc/syslog.confkern.=debug -/var/log/bandwidth
sources
http://doxfer.webmin.com/Webmin/LinuxFirewall
http://www.adella.org/spip/Configurer-IPTABLES-avec-WEBMIN
http://ubuntuforums.org/archive/index.php/t-1442954.html
http://fsse.info/IpTables
http://fsse.info/WebMinFirewall
http://www.linuxhomenetworking.com/wiki/index.php/Quick_HOWTO_:_Ch14_:_Linux_Firewalls_Using_iptables
Nat transparent
/etc/network/interfaces
# This file describes the network interfaces available on your system
# and how to activate them. For more information, see interfaces(5).
# The loopback network interface
auto lo
iface lo inet loopback
#interface internet
auto eth0
iface eth0 inet static
address 172.16.1.226
network 172.16.1.0
broadcast 172.16.1.255
netmask 255.255.255.0
gateway 172.16.1.254
#interface LOCAL
auto eth1
iface eth1 inet static
address 10.0.0.1
network 10.0.0.0
broadcast 10.0.255.255
netmask 255.255.0.0
gateway 172.16.1.254
#gateway 10.0.0.1
#pre-up /home/manager/iptables.start
#!/bin/bash
#sysctl net.ipv4.ip_forward=1
#iptables -> /etc/init.d/iptables
#sudo update-rc.d iptables defaults
#eth0 internet
iptables -A POSTROUTING -t nat -o eth0 -j MASQUERADE
nameserver 172.16.1.254
/etc/dhcp3/dhcpd.conf
#
# Sample configuration file for ISC dhcpd for Debian
#
# Attention: If /etc/ltsp/dhcpd.conf exists, that will be used as
# configuration file instead of this file.
#
# $Id: dhcpd.conf,v 1.1.1.1 2002/05/21 00:07:44 peloy Exp $
#
# The ddns-updates-style parameter controls whether or not the server will
# attempt to do a DNS update when a lease is confirmed. We default to the
# behavior of the version 2 packages ('none', since DHCP v2 didn't
# have support for DDNS.)
ddns-update-style none;
# option definitions common to all supported networks...
#option domain-name "8.8.8.8";
#option domain-name-servers ns1.example.org, ns2.example.org;
default-lease-time 600;
max-lease-time 7200;
# If this DHCP server is the official DHCP server for the local
# network, the authoritative directive should be uncommented.
#authoritative;
# Use this to send dhcp log messages to a different log file (you also
# have to hack syslog.conf to complete the redirection).
log-facility local7;
# No service will be given on this subnet, but declaring it helps the
# DHCP server to understand the network topology.
#subnet 10.152.187.0 netmask 255.255.255.0 {
#}
# This is a very basic subnet declaration.
subnet 10.0.0.0 netmask 255.255.0.0 {
range 10.0.0.2 10.0.10.254;
option routers 10.0.0.1;
option domain-name "salle 416";
option domain-name-servers 8.8.8.8;
}
# This file describes the network interfaces available on your system
# and how to activate them. For more information, see interfaces(5).
# The loopback network interface
auto lo
iface lo inet loopback
#interface internet
auto eth0
iface eth0 inet static
address 172.16.1.226
network 172.16.1.0
broadcast 172.16.1.255
netmask 255.255.255.0
gateway 172.16.1.254
#interface LOCAL
auto eth1
iface eth1 inet static
address 10.0.0.1
network 10.0.0.0
broadcast 10.0.255.255
netmask 255.255.0.0
gateway 172.16.1.254
#gateway 10.0.0.1
#pre-up /home/manager/iptables.start
#!/bin/bash
#sysctl net.ipv4.ip_forward=1
#iptables -> /etc/init.d/iptables
#sudo update-rc.d iptables defaults
#eth0 internet
iptables -A POSTROUTING -t nat -o eth0 -j MASQUERADE
/etc/dhcp3/dhcpd.conf
#
# Sample configuration file for ISC dhcpd for Debian
#
# Attention: If /etc/ltsp/dhcpd.conf exists, that will be used as
# configuration file instead of this file.
#
# $Id: dhcpd.conf,v 1.1.1.1 2002/05/21 00:07:44 peloy Exp $
#
# The ddns-updates-style parameter controls whether or not the server will
# attempt to do a DNS update when a lease is confirmed. We default to the
# behavior of the version 2 packages ('none', since DHCP v2 didn't
# have support for DDNS.)
ddns-update-style none;
# option definitions common to all supported networks...
#option domain-name "8.8.8.8";
#option domain-name-servers ns1.example.org, ns2.example.org;
default-lease-time 600;
max-lease-time 7200;
# If this DHCP server is the official DHCP server for the local
# network, the authoritative directive should be uncommented.
#authoritative;
# Use this to send dhcp log messages to a different log file (you also
# have to hack syslog.conf to complete the redirection).
log-facility local7;
# No service will be given on this subnet, but declaring it helps the
# DHCP server to understand the network topology.
#subnet 10.152.187.0 netmask 255.255.255.0 {
#}
# This is a very basic subnet declaration.
subnet 10.0.0.0 netmask 255.255.0.0 {
range 10.0.0.2 10.0.10.254;
option routers 10.0.0.1;
option domain-name "salle 416";
option domain-name-servers 8.8.8.8;
}
Inscription à :
Commentaires (Atom)















